Cloud computing is no longer an optional technology for enterprises. It is the foundation of digital operations, enabling scalability, global collaboration, data-driven decision-making, and rapid innovation. However, as enterprises move more critical workloads to the cloud, security risks continue to grow in parallel. Threat actors are becoming more advanced, cloud environments more complex, and regulatory expectations more demanding.
For large organizations, cloud security is not just about protecting infrastructure—it is about safeguarding business continuity, customer trust, and long-term growth. This is why enterprises must adopt structured, forward-looking security strategies rather than relying on ad hoc controls.
This article explains the most important cloud security principles enterprises must follow, highlights current threat trends, and outlines actionable best practices that align with modern cloud environments.
Why Cloud Security Has Become a Strategic Enterprise Concern
Enterprise cloud environments differ significantly from small or mid-sized deployments. They often involve multiple cloud providers, thousands of users, interconnected applications, and sensitive data spread across regions. This scale amplifies the impact of even minor security gaps.
Modern enterprises also rely heavily on automation, APIs, and AI-driven workloads. While these technologies improve efficiency, they also expand the attack surface. A single compromised identity or misconfigured service can expose large volumes of data or disrupt critical business operations.
As a result, cloud security is no longer just an IT responsibility. It is a board-level concern tied directly to financial risk, compliance exposure, and brand reputation.
How Enterprise Cloud Threats Are Evolving
The cloud threat landscape has shifted dramatically in recent years. Attackers are no longer focused solely on exploiting software vulnerabilities. Instead, they target operational weaknesses that emerge from complexity and scale.
Key Trends Shaping Cloud Security Risks
-
Identity-based attacks have overtaken network-based attacks
-
Misconfigurations remain the leading cause of cloud breaches
-
Ransomware groups increasingly target cloud backups and workloads
-
Third-party integrations introduce indirect attack paths
-
Automated attacks exploit cloud resources faster than manual defenses can respond
These trends highlight why enterprises must move beyond reactive security models.
Leading Causes of Enterprise Cloud Security Incidents (2026 Trend)

This trend shows that most cloud incidents are preventable through governance, identity controls, and continuous monitoring.
Understanding the Shared Responsibility Model Clearly
A common source of enterprise cloud risk is misunderstanding who is responsible for what. Cloud providers secure the physical infrastructure and core services, but enterprises are responsible for securing everything they deploy.
This includes:
-
User access and permissions
-
Application security
-
Data protection
-
Configuration management
-
Compliance controls
Failure to understand this model leads to gaps that attackers routinely exploit.
Must-Follow Cloud Security Tips for Enterprises
Enterprises need a layered, proactive approach to cloud security. The following Cloud Security Tips represent essential practices that every large organization should adopt.
1. Make Identity the Core Security Control
In modern cloud environments, identity is the primary security boundary. Employees, contractors, applications, and automated services all access cloud resources through identities.
Enterprises should:
-
Enforce multi-factor authentication across all accounts
-
Apply least-privilege access policies
-
Eliminate unused and over-permissioned accounts
-
Secure machine and service identities
Strong identity governance reduces the risk of lateral movement and unauthorized access.
2. Apply Zero Trust Principles Across Cloud Environments
Zero Trust assumes that no user or system should be trusted by default, regardless of location. Every access request must be verified continuously.
This model is especially effective for enterprises operating hybrid and multi-cloud environments. It limits blast radius during breaches and improves visibility into access patterns.
Zero Trust is no longer a future concept—it is a practical necessity.
3. Continuously Manage Cloud Configurations
Cloud environments change constantly. Manual reviews cannot keep pace with enterprise-scale operations.
Continuous configuration management allows organizations to:
-
Detect insecure settings in real time
-
Enforce security baselines automatically
-
Prevent configuration drift across teams and regions
This is one of the most impactful Cloud Security Tips, as misconfigurations remain the top cause of cloud incidents.
Security Risk Over Time With and Without Configuration Monitoring
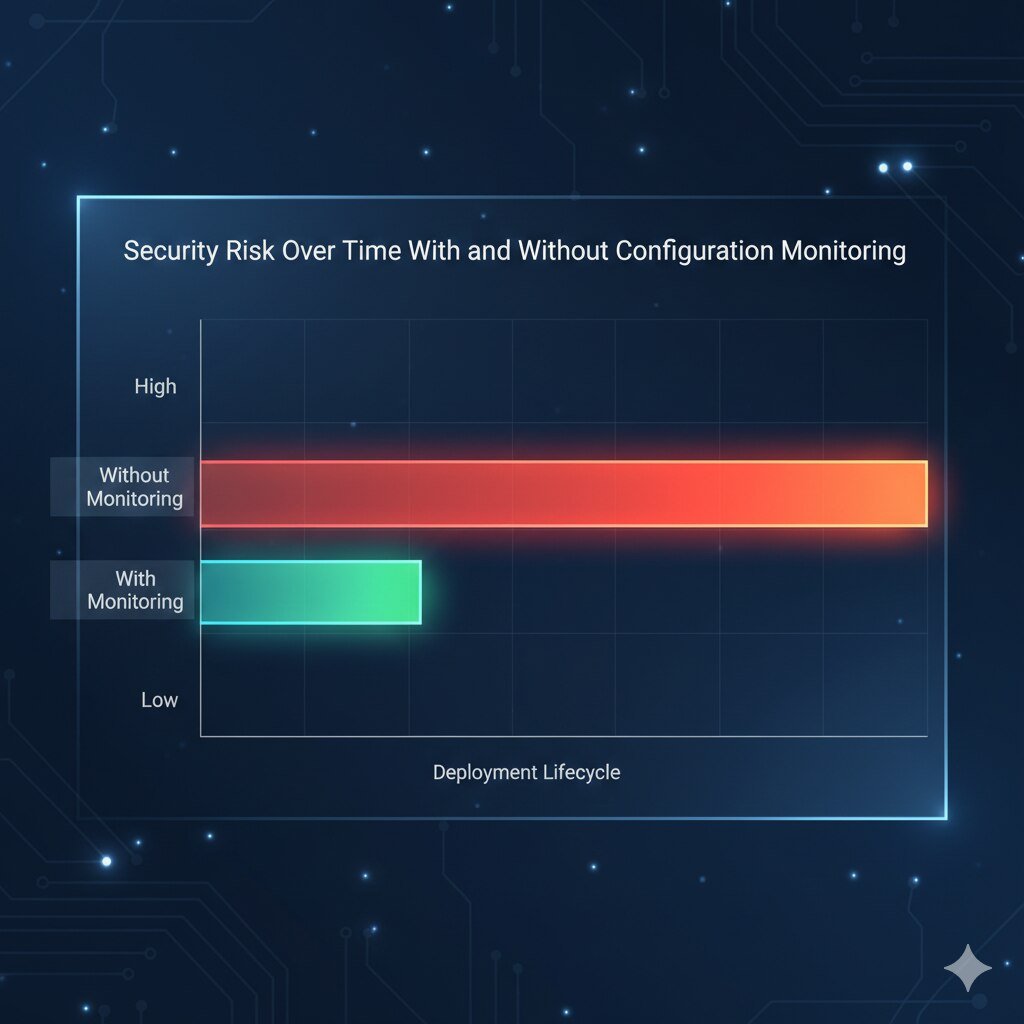
Automated monitoring dramatically reduces long-term risk exposure.
4. Protect Data Throughout Its Lifecycle
Enterprises store, process, and move data constantly within cloud environments. Protecting that data requires controls at every stage.
Best practices include:
-
Encrypting data at rest and in transit
-
Applying strict access controls to sensitive datasets
-
Monitoring data movement across services and regions
Data protection is not just a technical issue—it is also a regulatory and reputational one.
5. Centralize Logging and Security Visibility
Visibility is the foundation of effective cloud security. Without it, threats remain undetected until damage is already done.
Enterprises should:
-
Centralize logs from all cloud services
-
Monitor user behavior and workload activity
-
Correlate events across environments
Centralized visibility enables faster detection, investigation, and response.
6. Secure APIs and Automation Pipelines
APIs and CI/CD pipelines are critical components of enterprise cloud environments. They also represent high-value attack targets.
Security measures should include:
-
Strong authentication for APIs
-
Secrets management for automation tools
-
Security scanning within CI/CD pipelines
Ignoring automation security can undermine even the strongest perimeter controls.
Enterprise Attack Surface Expansion

As automation increases, so does the need for stronger security controls.
7. Align Cloud Security With Compliance Requirements
Enterprises must meet strict regulatory standards such as GDPR, HIPAA, PCI DSS, and industry-specific frameworks.
Cloud security programs should support:
-
Continuous audit readiness
-
Data residency and sovereignty requirements
-
Incident reporting obligations
Security and compliance should reinforce each other, not operate in silos.
8. Use Automation and AI for Faster Threat Response
Enterprise cloud environments generate massive volumes of security data. Manual analysis is no longer feasible.
Automation and AI help by:
-
Detecting anomalies in real time
-
Responding to threats consistently
-
Reducing response time during incidents
When used responsibly, AI strengthens defensive capabilities and improves resilience.
9. Invest in Cloud Security Skills and Culture
Technology alone cannot secure cloud environments. Human error remains one of the biggest risk factors.
Enterprises should:
-
Train employees on cloud security awareness
-
Educate developers on secure cloud architecture
-
Encourage shared responsibility across teams
A strong security culture amplifies the effectiveness of all technical controls and reinforces Cloud Security Tips throughout the organization.
10. Prepare for Incidents Before They Happen
No enterprise can guarantee complete prevention. What matters is preparedness.
Effective incident response planning includes:
-
Clearly defined roles and responsibilities
-
Automated containment processes
-
Regular testing and simulations
Prepared organizations recover faster and suffer less damage during security events.
Impact of Incident Preparedness

Preparation significantly reduces business disruption.
Why These Practices Matter for Enterprise Growth
Strong cloud security enables:
-
Stable operations
-
Regulatory confidence
-
Customer trust
-
Faster innovation
By consistently applying proven Cloud Security Tips, enterprises can reduce risk while supporting digital transformation.
Conclusion
Cloud security has become one of the defining challenges for modern enterprises. The combination of scale, automation, and evolving threats demands a disciplined, proactive approach. Enterprises that rely on outdated security models expose themselves to unnecessary risk.
By prioritizing identity, visibility, automation, governance, and continuous improvement, organizations can build resilient cloud environments. Following these Cloud Security Tips is not about compliance alone—it is about protecting the foundation on which enterprise success depends.
FAQs:
1. Why is cloud security important for enterprises?
Cloud security is important because enterprises store sensitive data and run critical workloads in the cloud, making them prime targets for cyberattacks and compliance risks.
2. What are the biggest cloud security risks for enterprises?
The biggest risks include misconfigurations, stolen credentials, insecure APIs, ransomware attacks, and lack of visibility across cloud environments.
3. How can enterprises reduce cloud security risks?
Enterprises can reduce risks by applying strong identity controls, continuous monitoring, encryption, automation, and proven Cloud Security Tips.
4. Is cloud security the responsibility of the cloud provider?
Cloud security is a shared responsibility. Providers secure the infrastructure, while enterprises must secure data, applications, identities, and configurations.
5. How often should enterprises review their cloud security posture?
Enterprises should continuously monitor cloud security and conduct regular reviews, audits, and testing to address new threats and configuration changes.
Read Dive is a leading technology blog focusing on different domains like Blockchain, AI, Chatbot, Fintech, Health Tech, Software Development and Testing. For guest blogging, please feel free to contact at readdive@gmail.com.





